Table of Contents
- ShinyHunters Targets Dating Giant Match Group in Bold SSO Vishing Attack
- Attack Vector: Voice Phishing Bypasses SSO Defenses
- ShinyHunters: Prolific Breach Actors with a Track Record
- Technical Breakdown: SSO Risks in Enterprise Environments
- Broader Impact on Dating Apps and Users
- Industry-Wide Lessons: Securing the SSO Perimeter
ShinyHunters Targets Dating Giant Match Group in Bold SSO Vishing Attack
On January 28, 2026, notorious hacking group ShinyHunters announced on dark web forums that they had breached Match Group, parent company of popular dating apps Match, Hinge, and OkCupid. The group claims to have extracted over 10 million user records, including user IDs, IP addresses, Hinge subscription transaction details like payment amounts, internal employee emails, and corporate contracts. This incident, reported just two days ago as of January 30, marks a significant escalation in attacks on consumer dating platforms, highlighting vulnerabilities in single sign-on (SSO) systems.
Attack Vector: Voice Phishing Bypasses SSO Defenses
ShinyHunters allegedly employed vishingvoice phishingto compromise Okta SSO credentials and access via AppsFlyer, a mobile analytics platform. Vishing involves phone calls impersonating trusted IT support to trick employees into revealing credentials or approving malicious access. Unlike traditional phishing emails, vishing exploits human trust in voice communication, often using spoofed caller IDs and social engineering scripts tailored from LinkedIn profiles or company directories.
Once inside, attackers navigated Match Group's SSO infrastructure, which centralizes authentication across services. SSO simplifies user logins but creates a single point of failure: one compromised credential grants broad access. Match Group confirmed they terminated the unauthorized access swiftly after the claims surfaced, estimating the intrusion began mid-January. Crucially, no user login credentials, financial details, or private messages appear compromised, classifying the breach as 'informational' per company statements.
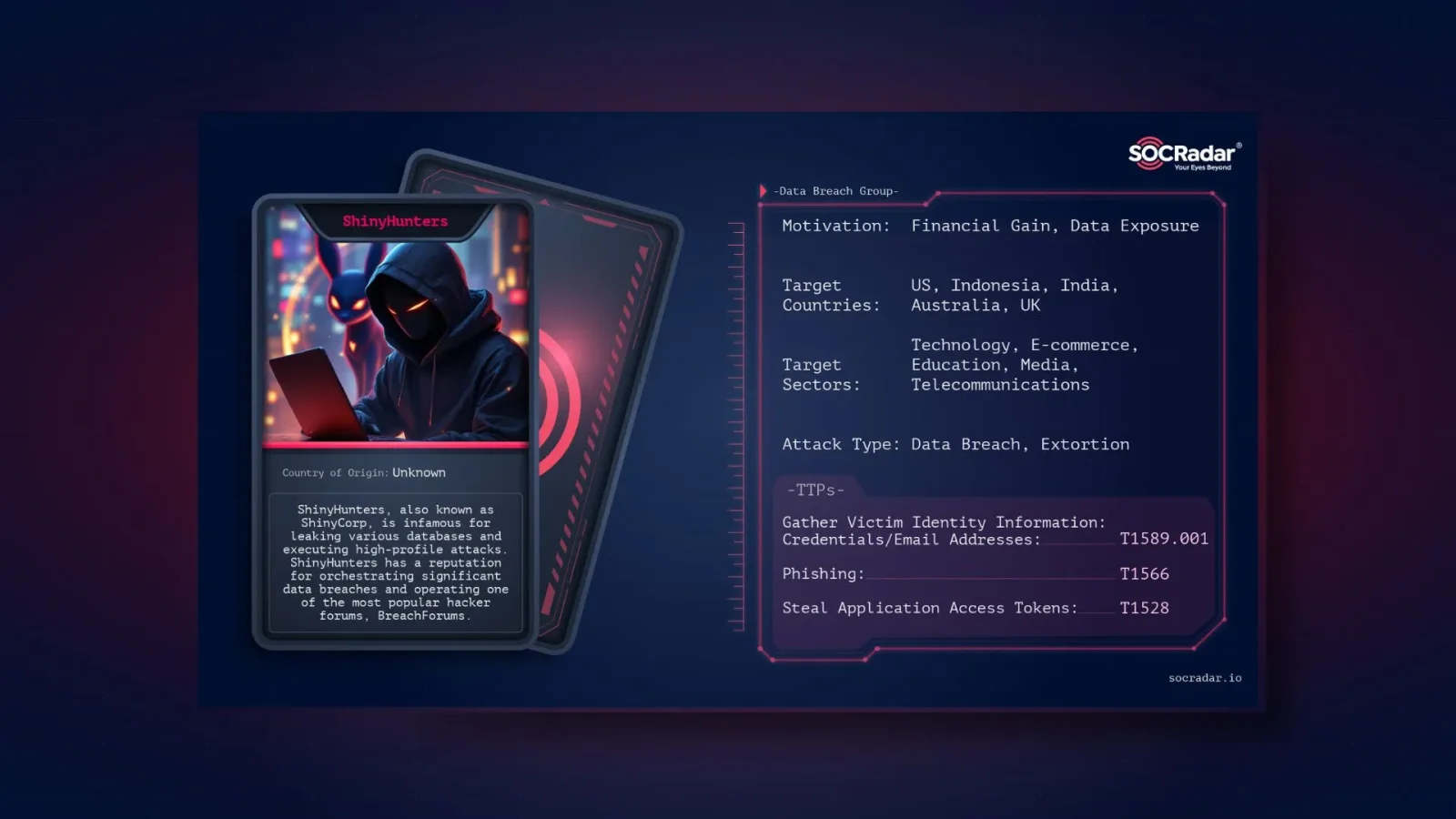
ShinyHunters: Prolific Breach Actors with a Track Record
Active since 2020, ShinyHunters (aka Scattered Spider or UNC3944) specializes in high-profile data thefts. Past victims include AT&T (73M records, 2024), Ticketmaster (560M users), and Santander Bank. Their tactics blend social engineering with technical exploits, often targeting helpdesks or contractors. In this case, the group followed a pattern seen in recent Panera Bread claims (14M records via SSO) and a 149M credential cache exposure, both tied to identity compromises rather than perimeter breaches.
The group's motive appears dual: extortion via data sales on BreachForums and notoriety to attract buyers. They leaked samples proving access, including Hinge transaction IDs and employee emails, pressuring Match for ransomthough no payment demands have been publicly confirmed yet.
Technical Breakdown: SSO Risks in Enterprise Environments
- Okta SSO Exposure: Okta, a leading identity provider, manages federated logins. Compromised admin tokens allow token replay attacks, impersonating users across apps.
- AppsFlyer Role: This platform tracks app installs and events; breached analytics data revealed user behaviors and IPs, aiding further targeting.
- Data Scope: 10M+ records include non-sensitive fields, but IP logs enable geolocation profiling, and transaction data risks payment tracing if combined with other leaks.
- Mitigation Gaps: Standard MFA often fails vishing, as attackers coerce one-time codes over phone. Phishing-resistant MFA (e.g., FIDO2 hardware keys) and just-in-time access are recommended.
Broader Impact on Dating Apps and Users
Dating apps handle intimate data: profiles, chats, payments. This breach follows Bumble investigations into similar ShinyHunters claims, signaling a campaign against the sector. Users face risks like targeted scams using exposed IPs or subscriptions for spear-phishing. For Match Group (NYSE: MTCH), stock dipped 2% post-announcement amid investor concerns over repeated incidentsHinge alone drives 40% of revenue.
Regulatory fallout looms: GDPR in Europe and CCPA in California mandate breach notifications within 72 hours. Match's response emphasizes no PII like passwords was hit, but experts urge full audits of SSO logs, endpoint detection, and employee training.
Industry-Wide Lessons: Securing the SSO Perimeter
This attack underscores 2026's trend: 70% of breaches start with identity compromise, per recent reports. Organizations must segment SSO scopes, enforce device trust, and deploy behavioral analytics to flag anomalous sessions. Consumers: Rotate passwords, enable app-based MFA, and monitor accounts via Have I Been Pwned.
For dating platforms, the stakes are personal. As ShinyHunters boasts 'fresh data for sale,' expect copycats. Match Group's quick remediation sets a positive example, but the incident exposes how vishing evades layered defenses in fast-scaling tech firms.